No technology has revolutionized the digital world like blockchain, not even arising anywhere close to what blockchain achieves. Blockchain raises many questions about its elements and operation, so we will delve a little into those responsible for maintaining the integrity of the network, who are known as Consensus Algorithms.
These consensus algorithms make all blockchain sequences different from each other. But the blockchain network has millions and millions of people in the same space, so how do these sequences operate without interfering each other? The answer lies in the architecture of the blockchain network, which was intelligently designed and the consensus algorithms are its core.
What is a Consensus Algorithm?
A consensus algorithm is the alternative by which blockchain achieves consensus. Public blockchains have gained popularity for their decentralized nature and function as distributed systems.
Since no central authority decides how it should behave, distributed blockchain nodes must “come to an agreement” to validate transactions. Consensus algorithms exist to ensure that each party works under protocol rules and transactions are confirmed, thus preventing the same money from being spent multiple times.
Difference Between Algorithm and Protocol
Many times these terms are confused with each other among those who inquire into this topic for the first time. The protocol is responsible for deciding the rules and the algorithm must tell the system how to comply with those rules to the letter. In other words, a blockchain’s consensus algorithm determines the validity of transactions and blocks.
Thus, Bitcoin and Ethereum are protocols, which have their own types of consensus algorithms to function properly.
In the Bitcoin case, the protocol defines how the nodes must interact and verifies the transmission of data, as well as what are the requirements for a block validation to be effective. While the consensus algorithm checks balances, signatures, and performs block validation.
Types of Consensus Algorithm
As indicated above, there are different consensus algorithms.
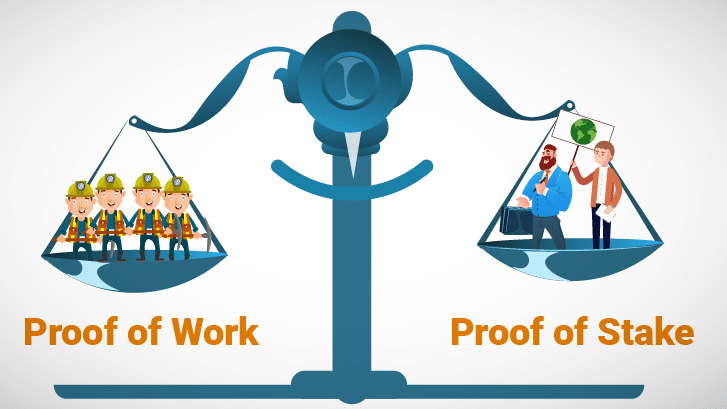
PROOF of WORK (PoW)
PoW is the first consensus algorithm created and is a critical part of Bitcoin and other cryptocurrency mining by regulating the obtaining of blocks. Proof of Work mining is the most historically used, the most relevant and the one that most people refer to when talking about cryptocurrency mining.
This popularity has been achieved thanks to its results in Bitcoin, Ethereum, Litecoin or Monero are some of the most popular on the market, which use Proof Of Work.
PROOF of STAKE (PoS)
The PoS consensus algorithm was developed in 2011 as an alternative to PoW and although they were created with the same objective, they differ greatly in terms of block validation.
PoS gives credit to those users who push the network and the platform into a better functioning. That is, those people who have a greater number of cryptocurrencies in the network, will have more facilities to get more blocks and rewards than newcomers.
PoS is special because it ensures that transactions with a certain cryptocurrency that is being mined remain within the platform and are stimulated over time. Thus, Proof of Stake also eliminates the problem of needing expensive machines that the smallest miners cannot afford and which, therefore, are adversely affected by the Proof of Work system.
Delegated PROOF of STAKE (dPoS)
Delegated Proof of Stake is a consensus protocol designed for highly scalable blockchains. This algorithm was created by Daniel Larimer in 2014. The implementation of this protocol offers Byzantine Fault Tolerance (BFT).
On the other hand, there are cryptocurrencies such as Ripple (XRP) that instead of working with blockchain, have their own system based on the RCPA (Ripple Protocol Consensus Algorithm), which also works to offer the RippleNet network and XRP a protocol with a certain Byzantine Fault Tolerance capacity.
Byzantine Fault Tolerance is the ability of a distributed computing system to withstand Byzantine faults, which can manifest as consensus failures, data verification failures, and network response protocol failures. The purpose of this tolerance is to solve these possible “bugs”.


![Basic Guide on Blockchain Consensus Algorithm - [The All You Need To Know]What is a Consensus Algorithm? 4 image](https://altsignals.io/wp-content/uploads/2025/10/blog-cta-card-scaled.webp)
![Basic Guide on Blockchain Consensus Algorithm - [The All You Need To Know]What is a Consensus Algorithm? 5 image](https://altsignals.io/wp-content/uploads/2025/10/blog-cta-card-mobile.webp)